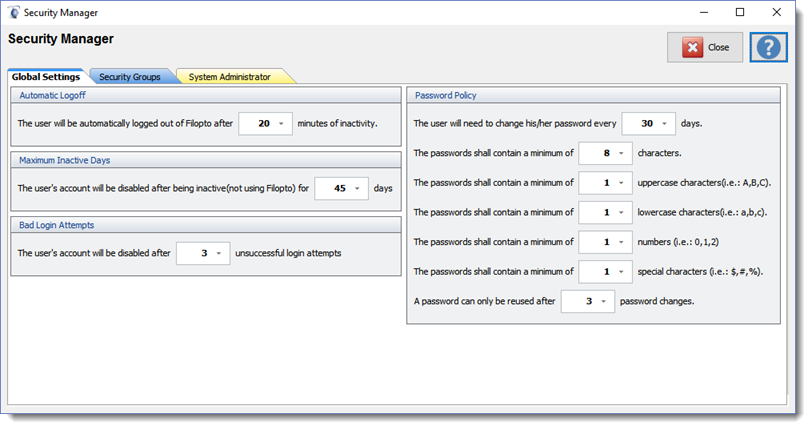
The Global Security Settings establishes the base security access policies that will be enforced by Filopto. The security access policies focuses on four (4) security requirements:
1) User Automatic Log Off Policy
2) User Account Deactivation Policy
3) Lockout Policy for Bad Login Attempts
4) Password Security Policy
IMPORTANT:
The default values represent the minimum values typically used in the industry. Various jurisdictions have specific requirements or recommendations for the various policies listed. Please review the rules applicable to your situation when setting the values to be used. For more information you may consult the documents associated with HIPAA, PIPEDA, CMS, PHI legislation as well as your professional association recommendations.
Review password requirements on how to achieve a secure password : Create a Secure Password
|
Automatic Log Off
Some legislation requires users PC's screens to be blanked out when not in use as to not permit non-authorized users to view the data displayed on the screen. This rule can be easily enforced by setting the Windows default screen saver to appear after x period of time of inactivity.
The above basic security policy is in many jurisdictions further enhanced by requiring users to log off after x period of time inactivity thus ensuring that a non-authorized user may not gain access to Patient information. The setting of this policy will automatically sign-off the user after the set elapsed time of inactivity.

Maximum Inactive Days
Some legislation requires users accounts to be terminated immediately when a user no longer works for the employer as well as if the user account has been inactive to a period of time. This setting addresses the situation of inactive accounts and permits the administrator to automatically deactivate the users account if it has not been used after x days. The administrator can always re-activate a user account that has been deactivated by using in the Employee Manager the Activate the User button.
Bad Login Attempts - Brute force attacks
The first line of defense against unauthorized users is a good password policy with active mitigation enforcement for attempts to break in to your system by guessing possible user passwords (also known as brute force attacks). This setting deactivates a user account after x number of failed password attempts during a consecutive 1 hour period. A user account can be reactivated by the administrator if the user forgot or used the incorrect password and exceeded the set limit by using in the Employee Manager the Activate the User button.
Password Policy
You have valuable information and it is your responsibility to protect it. A strong password policy is one of the basic steps in securing your data and meeting your legal responsibility. Review the Create a Secure Password help section to determine your password policy.
Change Passwords Every X
How often does a user need to change their password? It depends on how strong your password is. Stronger and longer password are less risky. But even strong passwords can be compromised. The longer the time period a password is active, the greater the risk that it can be compromised (somebody saw it or can guess it). This setting permits you to set the appropriate time frame for requiring your users to change their password.
How many days should I choose if I want user passwords to expire? Many organizations require new passwords every two or three months, Microsoft uses 42 days for its servers. When you change your password every few months, it limits how long a stolen password is useful to a stealthy attacker—how long he/she has access to your account. For help on your password policy see: Create a Secure Password
IMPORTANT:
Users can be exempted from the system wide password expiry policy by overriding the system default policy setting directly from within the employee profile. See Employee Profile - Security tab for more information
|
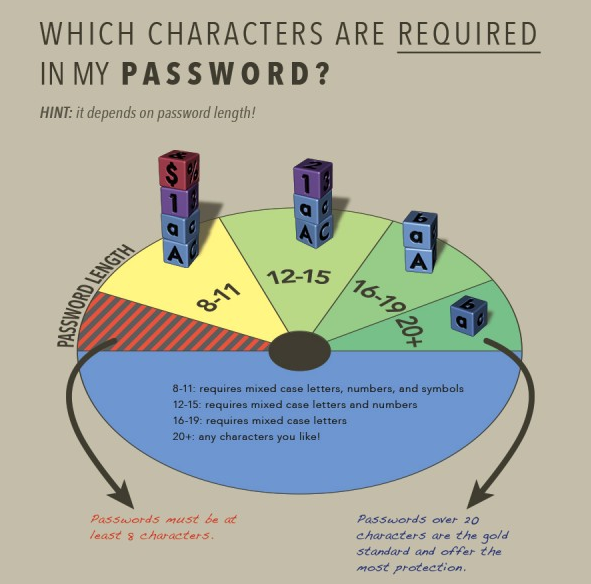
Create a Secure Password Policy
Passwords with less than 8 characters can typically be cracked instantly or within a few minutes. Test your password using this web site: https://howsecureismypassword.net/ to see how much time it takes to crack your password. Then consider your legal requirements and the security policy you want for your organization.
For more information on passwords see the Help file: How to Create a Secure Password.
.
Password can only be reused after X
Reusing the same passwords over and over again is not a good security policy. However when strong passwords are used and an acceptable time period has elapse the risk of reusing an old password is less. The administrator can define the security policy acceptable to their organization.